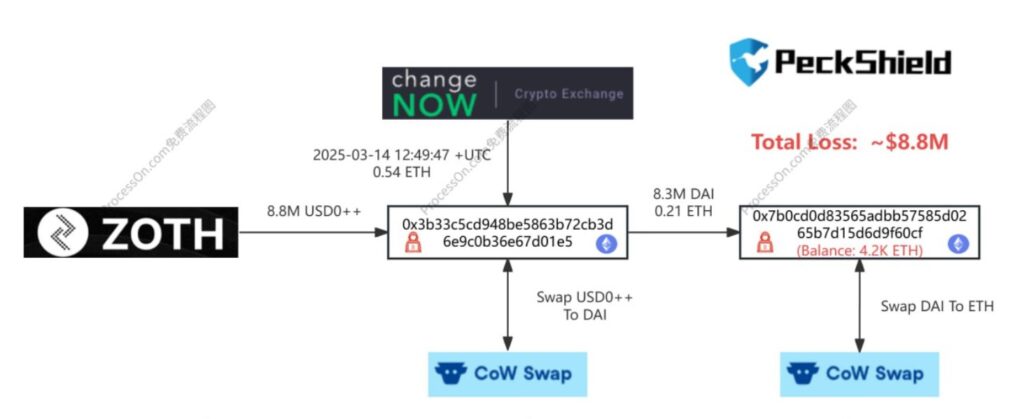
The cryptocurrency landscape has been shaken by a significant breach involving Zoth, a protocol focused on the re-staking of real-world assets. This alarming incident has resulted in losses exceeding .4 million, prompting the platform to enter maintenance mode as it addresses the aftermath of the attack.
A critical warning was issued by the blockchain security firm Cyvers, which flagged a suspicious transaction linked to Zoth on March 21. Their findings revealed that the protocol’s deployer wallet had been compromised, allowing an attacker to withdraw a staggering amount of digital assets.
Within minutes of the breach, the stolen funds were swiftly converted into DAI, a popular stablecoin, and then moved to an undisclosed wallet. In the wake of the exploit, Zoth has confirmed the security breach in a notice, assuring users that they are actively working to resolve the situation. The platform’s team is collaborating with partners to mitigate damage and has pledged to release a detailed report following a thorough investigation.
Cybersecurity experts, including Cyvers’ senior SOC lead Hakan Unal, noted that the compromise likely stemmed from a leakage of admin privileges. They reported that shortly before the hack was detected, a Zoth contract was upgraded to a malicious version orchestrated by a suspicious entity. This unique exploit enabled a bypass of standard security measures, granting full control over users’ funds almost instantaneously.
Experts have suggested a range of preventative measures, such as implementing multisignature contract upgrades and incorporating timelocks for contract modifications to reduce the risk of similar attacks in the future. Better key management practices are also essential to guard against unauthorized access.
The incident serves as a stark reminder of the vulnerabilities present within the decentralized finance (DeFi) sector, as certain security loopholes, like admin key compromises, continue to pose substantial threats. Unal emphasized that without decentralized upgrade mechanisms, DeFi platforms may remain at risk of sophisticated attacks targeting privileged roles.
This troubling event unfolds as the cryptocurrency community grapples with ongoing concerns about security and the integrity of decentralized systems, marking another pivotal moment in the evolving narrative of digital finance.
Zoth Protocol Exploit: Key Points and Implications
The recent exploit of the real-world asset re-staking protocol Zoth has raised significant concerns within the cryptocurrency community. Here are the key points regarding the incident:
- Losses Incurred:
Over .4 million in crypto assets were stolen following a breach in the Zoth protocol.
- Timing of the Exploit:
The suspicious transaction was flagged by blockchain security firm Cyvers on March 21, and the attack was executed shortly thereafter.
- Compromised Deployers:
The protocol’s deployer wallet was compromised, allowing the attacker to withdraw assets swiftly.
- Asset Conversion:
The stolen assets were converted into DAI stablecoin and subsequently transferred to a different address within minutes.
- Website Status:
Zoth’s website was put in maintenance mode following the security breach as the team worked to address the issue.
- Investigation and Response:
The Zoth team has committed to working with partners to mitigate the impact and will publish a detailed report following their investigation.
- Nature of the Hack:
The hack may have been caused by a leak in admin privileges, allowing the attacker unprecedented access.
- Need for Improved Security:
Experts emphasize the importance of better security measures in smart contract protocols to prevent similar incidents.
- Risk in DeFi Ecosystem:
Admin key compromises remain a major risk, highlighting vulnerabilities in decentralized finance.
“Without decentralized upgrade mechanisms, attackers will continue targeting privileged roles to take over protocols.” – Hakan Unal, Cyvers Alerts Senior SOC Lead
This incident may impact readers by emphasizing the need for vigilance and understanding of security risks in the crypto space. As the DeFi sector grows, it’s crucial for users and investors to be aware of potential vulnerabilities and the importance of platforms adopting robust security measures to protect their assets.
Vulnerability Exposed: Zoth’s Exploit vs. Industry Standards
The recent security breach in the Real-world asset (RWA) re-staking protocol Zoth has drawn attention to vulnerabilities plaguing the decentralized finance (DeFi) sector. With losses exceeding .4 million, this incident underscores a significant challenge faced across the industry—admin privilege leaks. While similar exploits have been reported in the past, Zoth’s case stands out due to the speed at which the stolen assets were converted into stablecoins and moved, revealing a systemic issue of technical flaws that many projects still grapple with.
What makes Zoth a critical case study for the DeFi landscape is not only the scale of the exploit but also the specific method employed. The attack utilized compromised administrative controls, allowing an unauthorized version of the smart contract to be deployed. Comparatively, other projects have sometimes managed to defend against such vulnerabilities through improved security measures such as multisig contracts and timelock upgrades—tactics that experts recommend as essential to bolster defense against similar breaches. The failure in Zoth’s security protocols may act as a cautionary tale for other projects that are vulnerable to similar attacks.
For investors and users of the Zoth platform, this incident presents considerable challenges. Trust has been severely undermined, which could deter potential users or investors who are evaluating various platforms within the DeFi realm. On the flip side, rival innovations may benefit as former Zoth users seek out alternatives known for their robust security mechanisms, leading to a potential influx of users toward platforms prioritizing security. Conversely, well-established projects can leverage this situation to build rapport and trust within the community, as they are not facing the same level of scrutiny.
For the wider DeFi ecosystem, Zoth’s exploit raises critical questions about smart contract vulnerabilities and highlights the ongoing risks of administrative control. Security specialists are likely to push for enhanced protocol standards, making the case for requiring stronger governance frameworks within similar projects to prevent future breaches. Such a shift could pave the way for a more secure DeFi landscape, potentially benefiting users in the long run but also creating hurdles for protocols that are slow to adapt to these necessary innovations.